Csp
CSP Textbook Notes
Big Idea 1: Creative Development
-
Computing innovations
-
Inspiration to create this shit is found everywhere😈😈😈
-
Constantly changing & improving
-
Applied in many other fields
-
Simulations
-
Cost-effective
-
Easier to do large num of tests
-
Con: does not account for all real-world variables
-
-
Health & medicine
-
Data analytics or smth
-
-
-
-
Hardware vs software
-
Physical components vs virtual instructions via programming lang
-
Computing innovation is about the software
-
Computing hardware has gotten smaller and more powerful over the years
-
Examples
-
Software
-
OS
-
Driverless vehicle software
-
Dual monitor programs for windows
-
Compiler
-
Graphics card driver
-
-
Hardware
-
Motherboard
-
Self-driving car
-
Monitor
-
Transistor
-
Graphics card
-
-
-
-
Collaboration
-
Helps people learn from each other
-
Diverse perspectives that avoid bias in computing development
-
For example, if the product is used by short and tall people, hiring only tall people to work on the product could bring bias; hiring both short and tall people brings new perspectives that may not have been achieved otherwise
-
-
Companies hire ppl who can code and have good collaboration skills
-
Effective collaboration can help one gain insight and knowledge by applying multiple perspectives, experiences, and skillsets
-
-
Collaboration is a learned skill
-
Includes communication, consensus building, conflict resolution, & negotiation
-
-
Collaboration can make others more self-aware
-
Matches weaknesses with someone elses strengths -> better product and new insight
-
-
Facilitates the solving of computational problems by applying multiple perspectives and skill sets
-
Combines different peoples resources. Talents & experiences
-
-
Not limited by location
-
Current computational tools allow people in diff physical locations to share data & info
-
-
-
How programs function
-
Program is often referred to as software
-
A collection of prgram statements that perform a specific task when run byt hte computer
-
Software is a set of instructions data or pgrams used to operate computers and execute specific tasks
-
-
Difficult to determine if a program works for every condition
-
Programmers can never have too many test cases
-
Logical errors demonstrate why collaboration si so important in programming
-
Common that a fresh set of eyes will be better than an entrenched programmer
-
-
A complex program can be described broadly by what it does
-
Keeping the program abstract helps the user focus on using the program instead of looking at the code
-
-
GUI is an example of abstraction, doesn’t show the user how it works
-
-
-
Program Input
-
This is data sent to a computer for processing by a program
-
Can come in multiple forms:
-
Tactile
-
User interaction
-
-
Audio
-
Visual
-
Text
-
-
Example of input/output
-
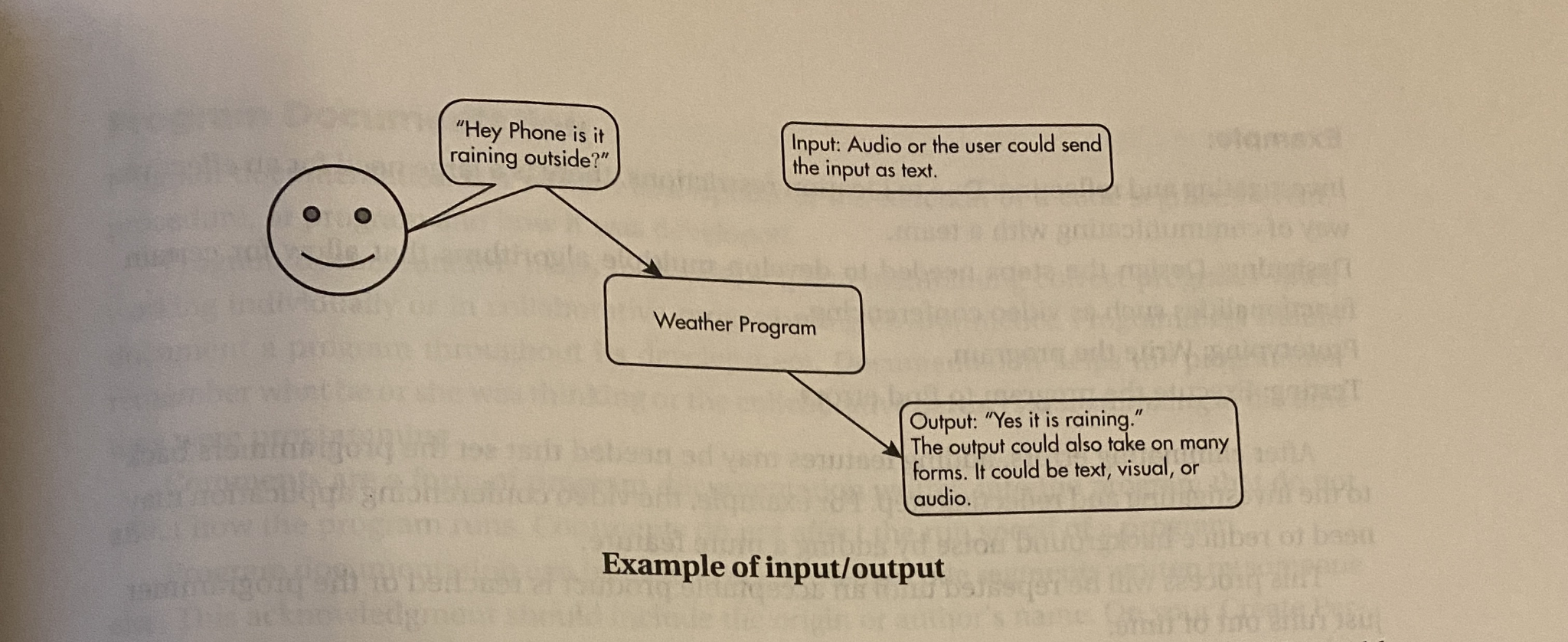
-
User says “hey phone” - triggers an event
-
The action that supplies input data to a program
-
Key press
-
Mouse click
-
Program is started
-
Anu other dewfinmed action taht affects the flow of execution
-
-
-
-
-
-
Development process
-
Can be ordered and intentional or exploratory in nature
-
A development process that is iterative requires refine ment and revisions based on feedback, testing, or reflection throughout the process, this may require revisiting earlier phases of the process
-
#1) investigating and reflecting ↡
-
#2 designing ↡
-
#3) prototyping ↡
-
#4) testing ↻
-
-
Example
-
#1) due to location restrictions, there is a large need for an effective way of communicating with a team
-
#2) design the steps needed to develop the multiple algorithms that allow for certain functionalities such as video conferencing
-
#3) write the program
-
#4) Execute the program to find errors
-
This process will be repeated until an acceptable product is reached or the programmer just runs out of time
-
-
-
A development process that is incremental is one that breaks the problem ito smaller pieces and makes sure each piece works before adding it to the whole
-
A program rarely works on the first development and breaking it into smaller parts of the code reduces the debugging process
-

-
Once they work, add the small chunks of code together to form the bigger program
-
-
The DESIGN of a program incorporates investigations to determine its reqs
-
Most programs are for ppl not progs and to meet the needs of ppl, investigation mus tidentify the prgram constraints & the concerns and interested of people who will uise the program
-
Example of perfomraing investigation
-
Colecting data in surveys
-
User testing
-
Interviews
-
Direct observations
-
-
Example of design phase
-
Brainstorming
-
Planning and storyboarding
-
Organizing the program into modules and function components
-
Creating diagrams that represent the layouts of the user interface
-
Developing a testing strat for the program
-
-
-
-
Program Documentation
-
A written desc of the func of a code segment, event, procedure, or program and how it was developed
-
Helps in developing and maintaining correct programs when working individually or in collaborative programming envs
-
Progs should document a program throughout its development - helps them rember what they were thinking
-
-
Comments
-
Form of program docs written in otthj epgram that do not affect how the program runs
-
Do not affect run speed
-
-
Can be used to acknowledge code segments written by someone else
-
Should include the origin or authors name
-
-
-
Program Errors
-
Three types of errors can occur
-
Logic error
-
Mistake in the algorithm or program that causes it to behave incorrectly or unexpectedly
-
-
Syntax Error
-
Mistake in the program where the rules of hte programming lang are not followed
-
-
Runtime Error
-
Mistake in the program that occurs during the execution of a program
-
Prog langs define their own runtime errors
-
-
-
Big Idea 2: Data
-
Bits represent data
-
Bit
-
Shorthand for a single binary digit and is etierh 0 or 1
-
-
Byte
-
8 bits
-
0111 0011 - contains 1 byte and 8 bits
-
-
Binary sequences
-
Can be used to represent all digital data/Anything that can be stored on a computer can be repped as by bin. seqs.
-
variable length
-
Example
-
Colors
-
Boolean logic
-
Lists & so on
-
-
-
-
Some data may take many bits to represent it
-
For example:
-
10 MP uses 10,000,000 pixels
-
1 pixel stores 6 bytes - 48 bits
-
MP is one billion pixels
-
-
This means that there are 8 bits * 6 bytes * 10m pixels - 480,000,000 bits in a single 10 MP picture.
-
(common for videos to use 1,00,000 bits/sec)
-
-
-
-
-
Abstractions
-
Bits are grouped to represent abstractions
-
EX:
-
Numbers
-
Chars
-
Colors
-
& so on
-
-
-
Abstractions find common features to generalize the program
-
Helps to shrink code & reduces the chance of error
-
Example:
-

-
The programming language is an abstraction of machine code & makes it easier to do stuff like add nums
-
-
-
-
Analog vs digital data
-
Ananalog signal
-
has values that change smoothly over time, rather than in discrete intervals
-
Ex:
-
Pitch
-
Volume
-
Colors
-
Position of a sprinter during a race
-
-
CONTINUOUS SIGNALS
-
-
Digital signals
-
An analog signal that has been broken up into steps
-
Analog data can closely approximate digital data using a sampling technique,
-
measuring values of the analog signal at regular intervals. The samples are measured to figure out the exact bits required to store each sample
-
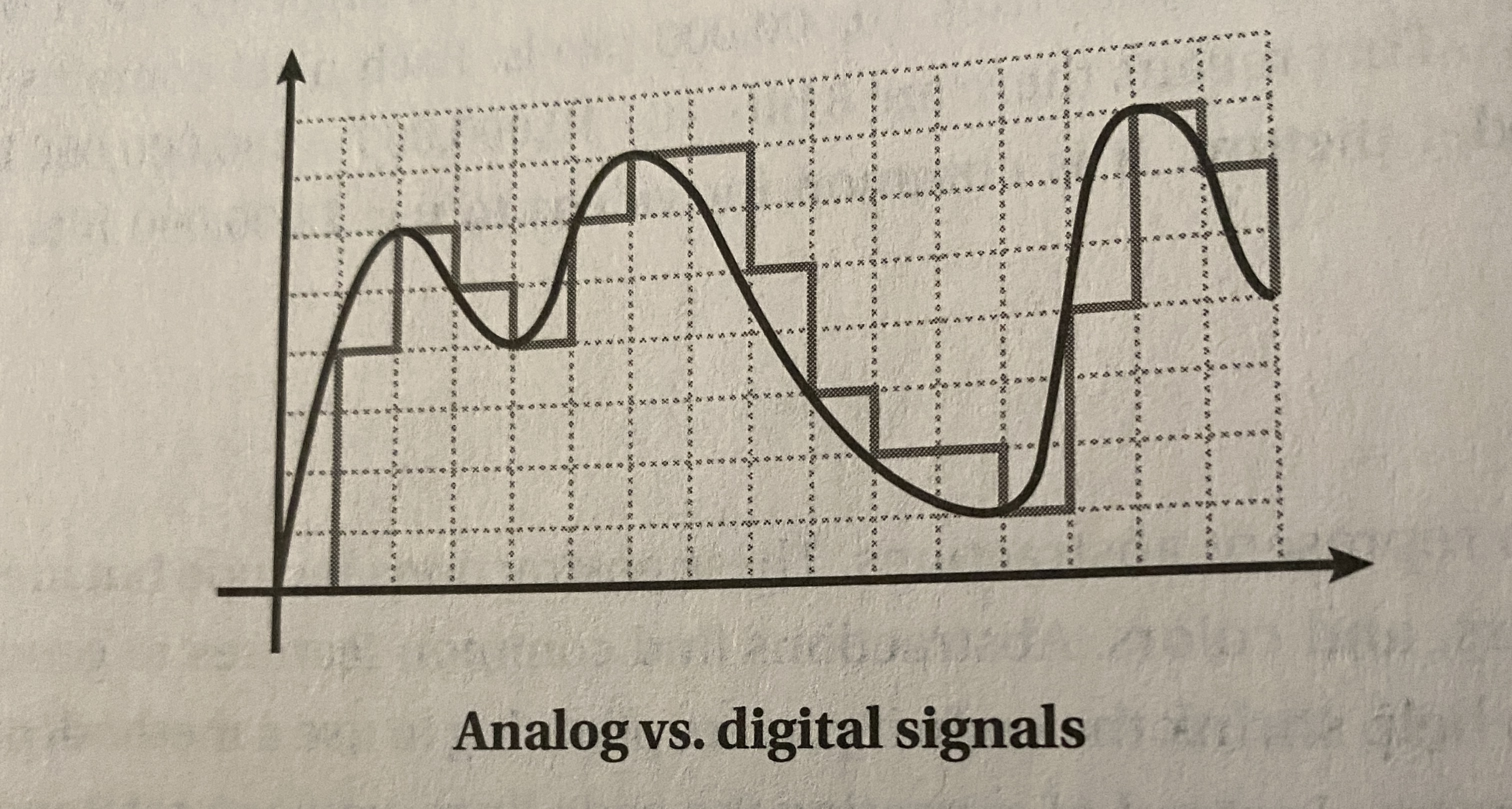
-
-
-
-
(the use of digital data to approximate real-world analog data is an example of an abstraction)
-
Consequences of using bits to represent data
-
A variable is an abstraction inside of a program that can hold a value
-
Each variable had associated data storage that represents one value, or can hold multiple vals inside of a larger val
-
EG:
-
Integer: 4
-
Real Number: 4.00
-
Boolean: True False -
String: “Novak the third”
-
List: [1, 1, 35, 6]
-
-
Integers are most often represented by a fix number of bits
-
Limits the num range of int vals & math operations on such values
-
Surpassing this limit throws an overflow error
-
AP Lang DOES NOT have num size limit - size of representable ints is limited ONLY by the szie of the computer’s memory
-
KNOW THAT SOME COMPUTER LANGS HAVE LIMITS ONT HE SIZE OF DATA TYPES FOR EXAM
-
-
-
-
Number Systems
-
Bin, decimal, & hexadec, are all used to represent and investigate digital data
-
KNOW HOW TO CONVERT BIN TO DEC AND DEC TO BIN FOR EXAM
-
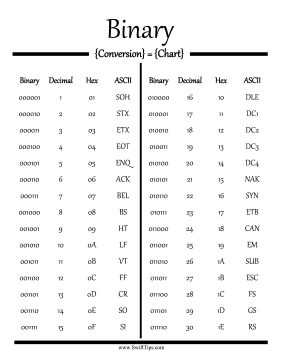
-
-
Various Errors
-
Several diff types of erroos can occur:
-
Overflow Errors
-
In many programming langs, a fixed num of bits is used to rep characters or int limits
-
when the number of bits is not enough to represent the number
-
EX:
-
On a 4-bit computer (largest num is 1111 or 7dec)
-
Running smth like
-
x=7
-
Y = x++
-
-
Returns an overflow error cuz its too large heheheaw
-
-
-
Run-time errors
-
A mistake in a program that happens when the program is run
-
EX: Accessing undeclared vars
-
-
-
Roundoff errors
-
Occurs when decimals (real nums) are rounded, one comp might round to a diff place than another
-
EX: ⅓ = 0.3333333333333333333 on one comp OR ⅓ 0.3333 on a diff comp
-
-
-
-
-
Lossy and Lossless Data compressions
-
Reducing the size (number of bits) of transmitted or stored data
-
(fewer bits does not necessarily mean less info)
-
-
Digital data compression often involves trade-offs in quality versus storage reqs
-
Lossy Compression
-
Can significantly reduce the file size for storage and transmission
-
Trade-off is that u will not recover the original file & SOME data will always be lost
-
Used in sitch where minimizing transmission time & data size is important
-
-
Lossless Compression
-
NO DATA IS LOST
-
Trade off is larger files that can be harder to store, transfer, and handle
-
Used in sitch where quality or ability to reconstruct the orig file is important
-
-

-
-
Information Extracted from Data
-
Computer programs can be used to process info & gain insight & knowledge
-
Info can include digital data such as
-
Geographic data
-
Premium data on social med sites based on usage
-
-
-
Information
-
The collection of facts and patterns extracted from data
-
-
Gaining insight from the above valuable involves a combination of…
-
Statistics
-
Mathematics
-
Programming
-
And problem solving
-
-
Large data sets may be analyzed computationally to reveal…
-
Patterns
-
Trends
-
Associations
-
(can me bisinterpereted)
-
(May show correlation between vars, does not mean a relationship exists)
-
(additional research is needed to determine the exact nature)
-
-
-
The size of the data sets often affects the amount of info that can be extracted
-
A single source does often does not contain the data needed to draw a conclusion
-
Combining data from a variety of sources may be necessary to have a conclusion
-
-
Depending on how the data was collected, the info may not be uniform (varying from test case to test case)
-
Data sets pose challenges regardless of size:
-
The need to clean data
-
Makes the data standardized (uniform) without needing to change anything
-
-
Incomplete data
-
Invalid data
-
The need to combine data sources
-
-
Data can get too large for traditional data-processing applications
-
(ability to process data depends on the capabilities of the users and their tools)
-
EX:
-
Social media activity generates an enormous amount of data and uses a data processing application
-
Too large to examine in hand in real-time
-
-
bias is often created by the types and sources of data being collected.
-
not eliminated by simply collecting more data since a large amount of data collected by humans will always reflect this bias
-
A large sample can magnify the bias associated with the data being used - can have little value if the sample is not representative of the population to which the results will be generalized
-
-
-
-
PRedicting algorithms
-
Use info collected from big data to influence our daily lives
-
EX:
-
A credit card company can use purchasing patterns to identify when to extend or flag a purchase for possible fraud
-
Social media sites can use patterns to target advertising based on viewing habits
-
-
-
-
Visualization of Data
-
Using appropriate visualizations when presenting digitally processed data can help one gain insight and knowledge
-
Data can lose their value if they cannot be presented in a way that can be interpreted
-
-
Can communicate info about data & make more complex data easier to interperet
-
Collum charts
-
Line graphs
-
Pie charts
-
XY charts
-
Radar charts
-
Histograms
-
waterfall charts
-
EX:
-
this company notices that greater users =- more profit so they can spend more of their resources on advertisements and attracting more users
-
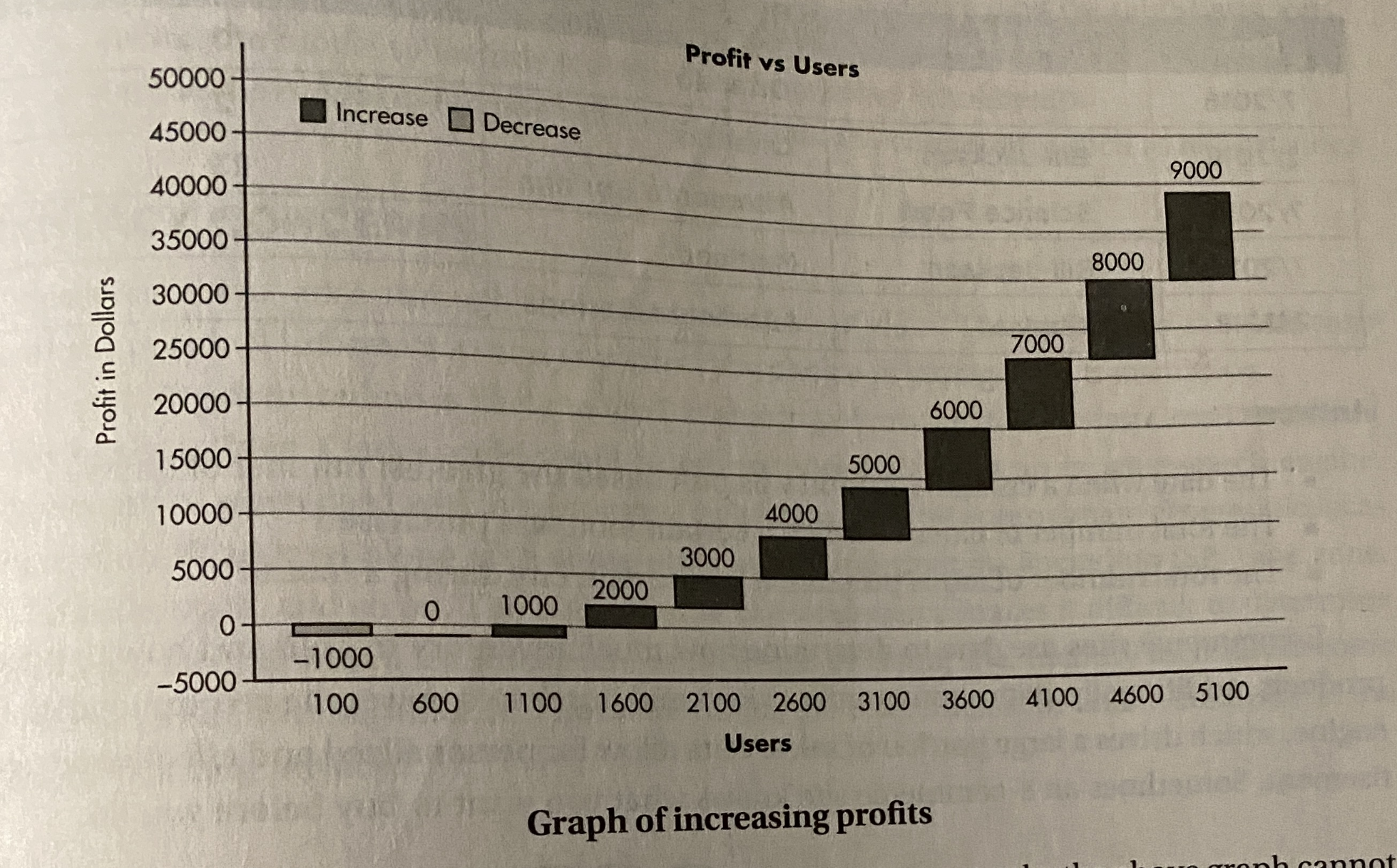
-
-
-
Predicting trends is not a guarrantee of future usage
-
(dangeruous to solely make decisions on good data rather than all data)
-
-
Use historical data to predict future events
-
Used to build a mathematical model that encompasses trends
-
This is used on current data to make predictions
-
-
-
-
Privacy Concerns
-
Arise through mass collection of data
-
May contain personal info
-
Can affect choice in storage and transmitting
-
-
-
Anything done online likely leads to the sharing of priv data
-
(trade off for the convenience of online shopping is the risk of violating privacy)
-
-
Metadata
-
data that describes data
-
EX:
-

-
Pic of dog is data
-
Filename, author, location, and time taken of this pic is metadata
-
-
Used for finding, roganizing, and managing info
-
Can Increase effective use of data by providing addition info ab varius aspects
-
Do not change primary data
-
BIG IDEA 3: Algorithms and Programming
-
Abstraction
-
Way to represent essential features without including the background details or explanations
-
Reduce complexity
-
Allow for efficient design
-
& implementation of complex systems
-
-
GUI is an example of abstraction
-
-
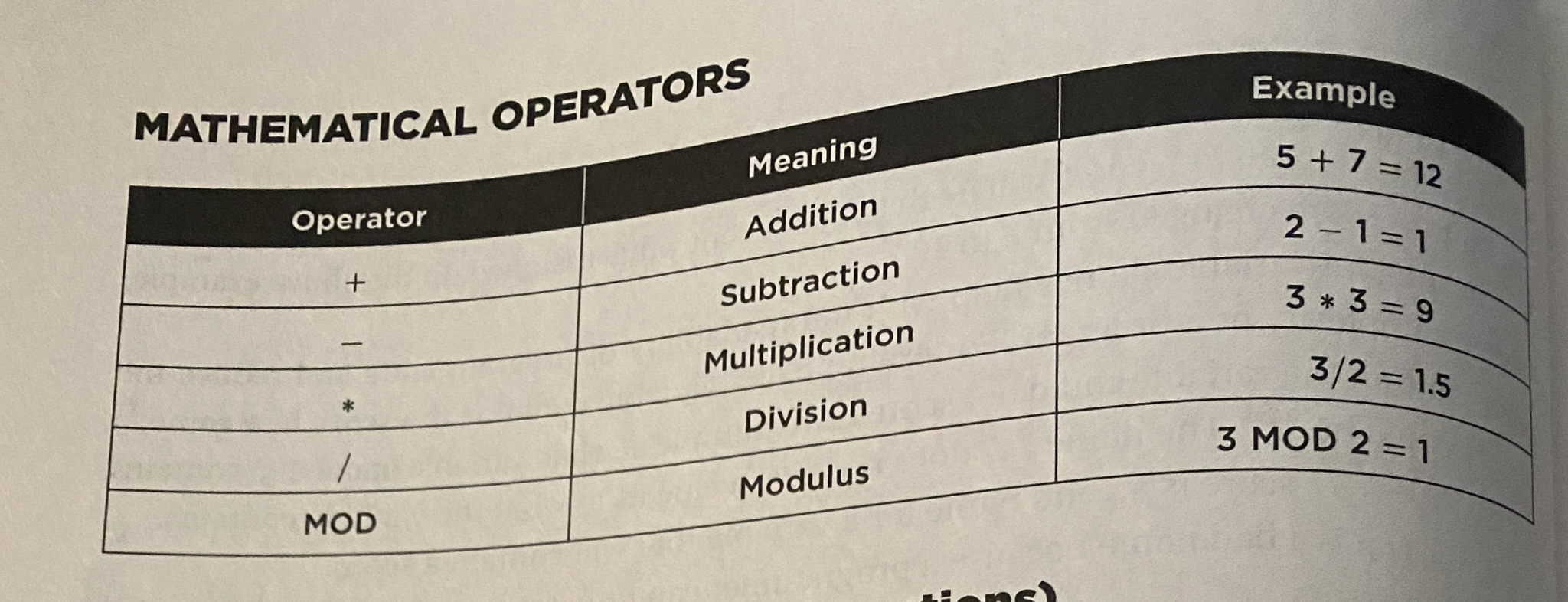
Math OPerators
-
-
Modulus Notes
-
If the dividend is a multiple of the divisor, then the return val is 0
-
If the dividend is smaller than the divisor, then the return val is the dividend itself
-
If teh divisor is 0, an ERROR is thrown
-
If 0 is the dividend, the return val is 0
-
-
Lists
-
START AT INDEX 1
-
Example of data abstraction
-
-
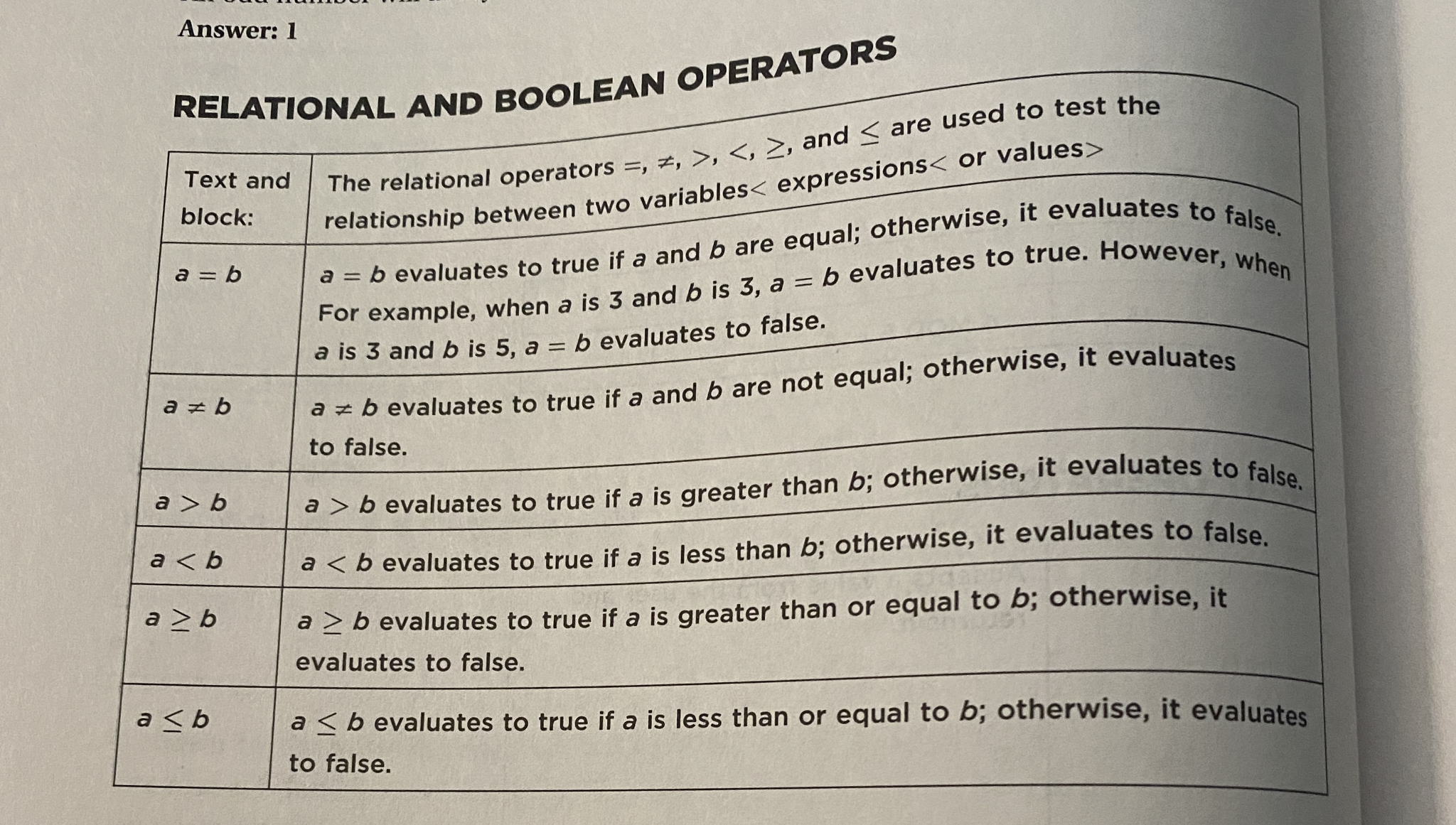
Relational and Bool Operators
-
-
Searching
-
Linear search (sequential search)
-
Finds an element in sorted or unsorted list
-
Sequentially checks EVERY element in the list
-
-
-
Binary Search
-
Finds element in a SORTED list
-
Halves the num of elements that need to be searched after comparing the desired val to the middle point.
-
If they are unequal, then the half in which the target cannot be is eliminated
-
-
-
-
BIG IDEA 4: Computer systems and Networks
-
Computing Devices
-
A computing device is a physical artifact that can run a program
-
Computers
-
Tabnlets
-
Servers
-
Routers
-
Smart sensors
-
-
Must be able to take inputs > process such inputs > calculate results based off such inputs
-
Not all computing devices are computers
-
Non-computer computing devices can be
-
Calculator
-
Printer
-
-
-
Compuing system
-
Group of omcputing devices and programs working together
-
Ex: a computer network
-
A group of interconnected computing devices capable of sending or receiving data
-
-
-
-
Autonomous Systems of the Internet
-
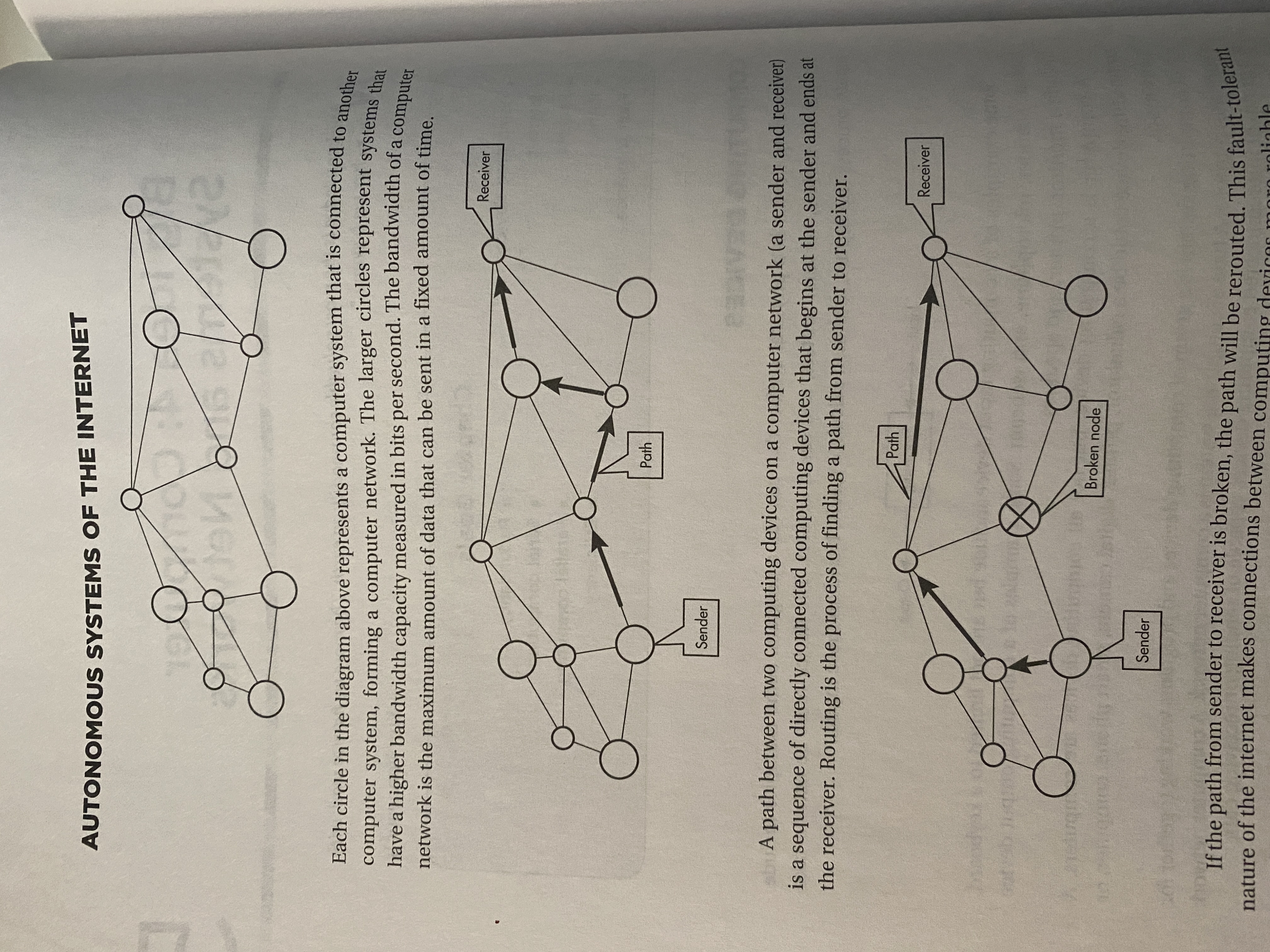 **
**
**-
This reps a computer network
-
Each circ is one computer system
-
Larger circs have larger bandwiths
-
Maximum amount of data that can be sent in a fixed amount of time
-
-
-
A path between two computing devices is a sequence of directly connected computing devices
-
Rounding is the process of finding a path form center to receiver
-
If path is broken, then the path will be rerouted (fault tolerant nature)
-
-
Internet conmnects devices and networks from all over the world
-
physical network of fiber optics, radio transmitters, and cabling
-
Devices and networks that make up the internet are connected and communicate using standardized, open communication protocols
-
An agreed-upon set of rules that specify the behavior of a system
-
-
These protocols have allowed for the internet to be scalable and meet new demands
-
-
-
Internet Protocol
-
Responsible for addressing and routing your online requests
-
A device is first assigned an IP before connecting to the internet
-
We are switching between the 4th and 6th version of the protocol (IPv4 && IPv6)
-
IPv4 stores addresses in 32 bits, 2^32 combinations
-
IPv6 stores addresses in 128 bits, 2^128 combinations
-
-
NOT PERMANENTLY ASSIGNED TO A USER AND CAN BE CHANGED AT ANY TIME
-
-
Transmission Control Protocol
-
Protocol defines how computers send packets to each other.
-
packets
-
Small chunks of data that are sent to other devices on a network (including the internet)
-
-
Guide the rules on how data are subdivided into small packets before transmission
-
-

-
-
User Datagram Protocol
-
Protocol that allows computer applications to send messages without checking fro missing packets
-
Saves time to retransmit missing packets
-
-
Not as reliable as TCP
-
-
Fault Tolerance
-
When a system can support failures and continue to func
-
The internet is designed to be fault tolerant
-
If one sys fails, a diff path can be chosen when routing
-
-
Redunancy
-
Inclusion of extra paths that can mitigate the failure of a system if other components
-
-
End-to-end architecture
-
The breaking down and assembly of packets at each end
-
The middle is hidden by abstraction
-
EXAMPLE:
-
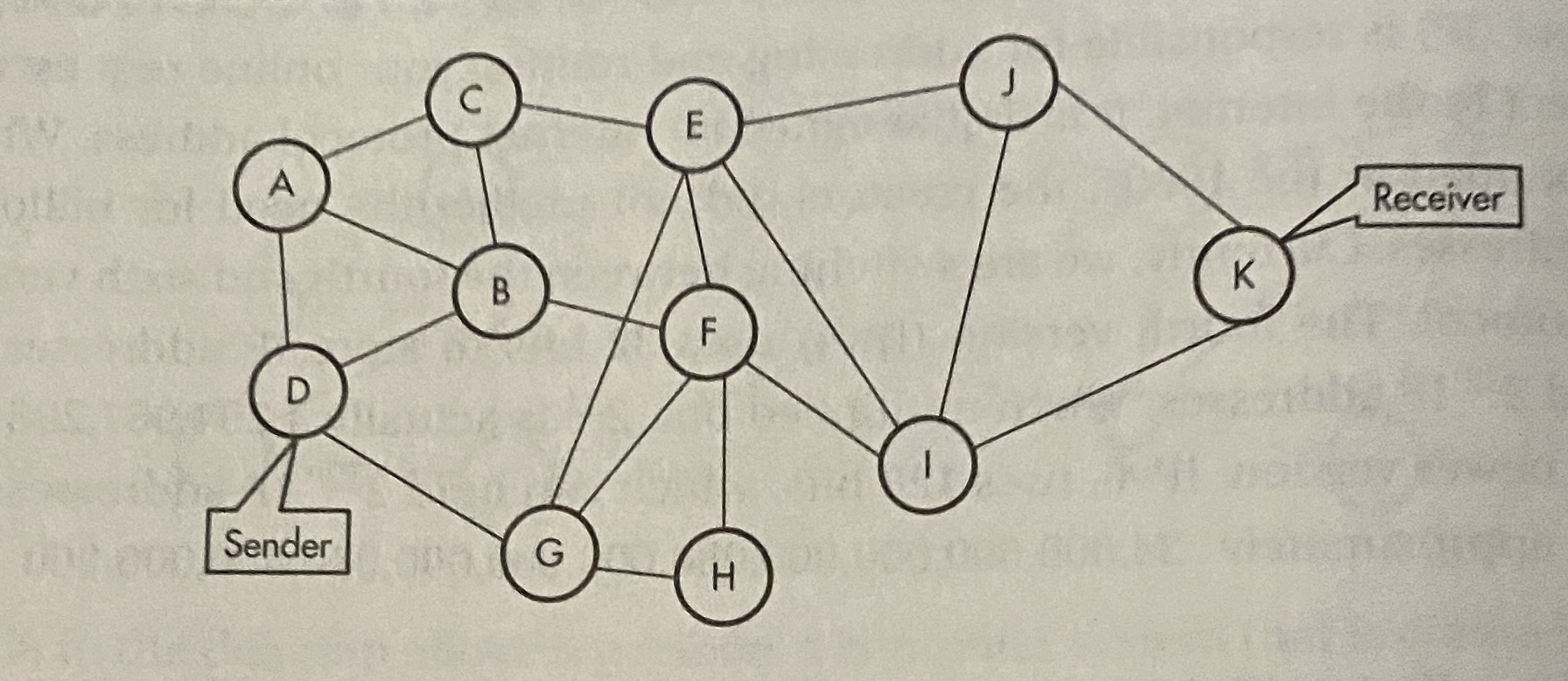
-
There are a multitude of paths that packets can take to travel between D (sender) and k(reciever)
-
Since there are multiple paths, packets are likely to arrive at the receiver out of order
-
-
If packets are not received, TCP will request the sender to resent the pissing packet
-
The IP of the send. And reciv. Are both in the header of the packet
-
-
When all packets are received, then the message will be reconstructed using their order found in the header
-
-
-
-
Difference between internet and world wide web
-
Internet refers to the hardware
-
Made up of computers, cables, routers, etc.
-
Glo0abl decentralized network that connects millions of computers
-
-
WWW refers to the software on the internet
-
HTTP is a protocol used by WWW to transmit data
-
Internet allows access to the WWW which is a system of linked pages, programs, and files
-
-
-
Efficiency of Solutions
-
Sequential computing
-
Computational model in which operations are performed in order, one at a time
-
Takes as long as the sum of all the steps
-
-
-
Parallle Computing
-
Involves breaking up a task into smaller, sequential pieces
-
These are then executed at the same time
-
Each on its own processor or on a set of computers that have been networked together
-
-
-
Takes AT LEAST as long as the longest branch in the prog
-
-
-
Sequential Computing
-
Problem broken into discrete instructures
-
Executed one by one by a single computing device
-
Having a sing CPU
-
-
-
Parallel Computing
-
Problem broken into discrete instructions
-
Executed concurrently by using multiple CPU
-
Takes as long as the longest task
-
Consist of a parallel portion and a sequential portion
-
A parallel computing solution takes as long as its sequential tasks + the long of its parallel tasks
-
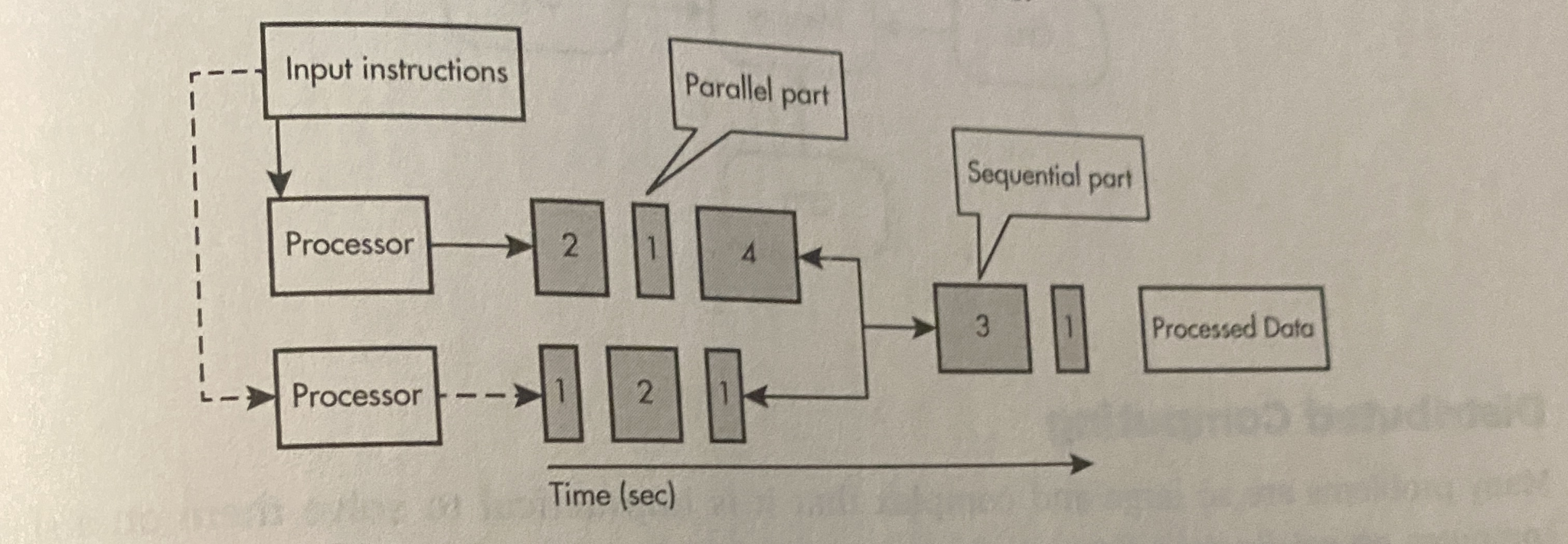
-
2+1+4+3+1 = 11 secs tot
-
-
-
Why is Parallel COmputing used?
-
Needed fro real world sims and modeling
-
Manyu things happen at the same time in the real world
-
-
EX:
-
Weather forecasting
-
Flight simulators
-
Car crash modeling
-
-
Speedup
-
Measured in the time to complete the task sequentially divided by the time to complete the task when done in parallel
-
SPEEDUP = (sequential run time)/(Parallel run time)
-
-
Efficiency is still limited by the sequential portion
-
Means that, at a certain point, parallel computing will not meaningfully increase efficientcy
-
-
-
Multiple processors can operate independently but share the same memory resources
-
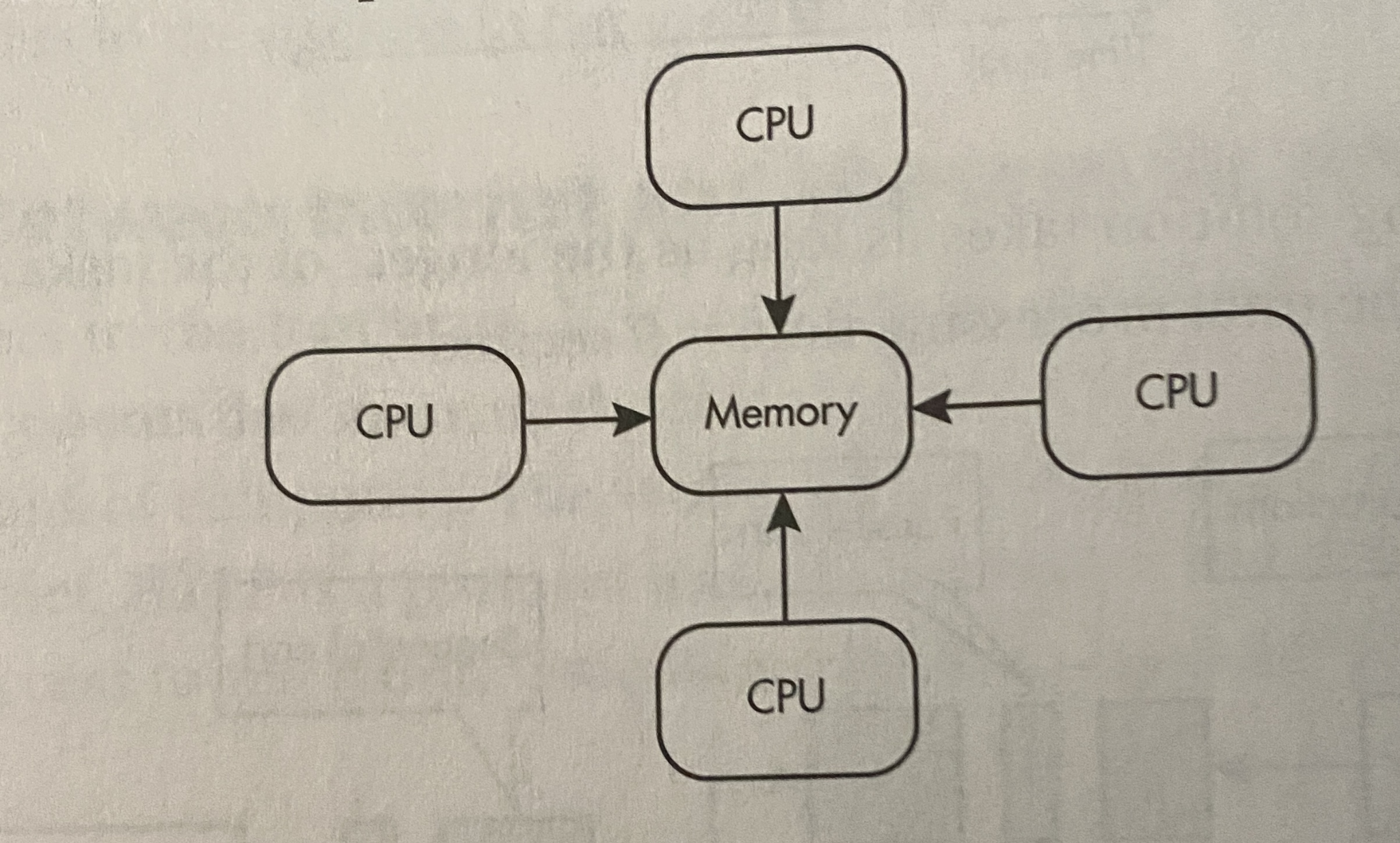 **
****
-
-
-
Distributed Computing
-
Computational model in which multiple devices are used to run a program
-
Many problems are too large and complex to be solved on a single computer
-
Bcz of processing time or storage
-
-
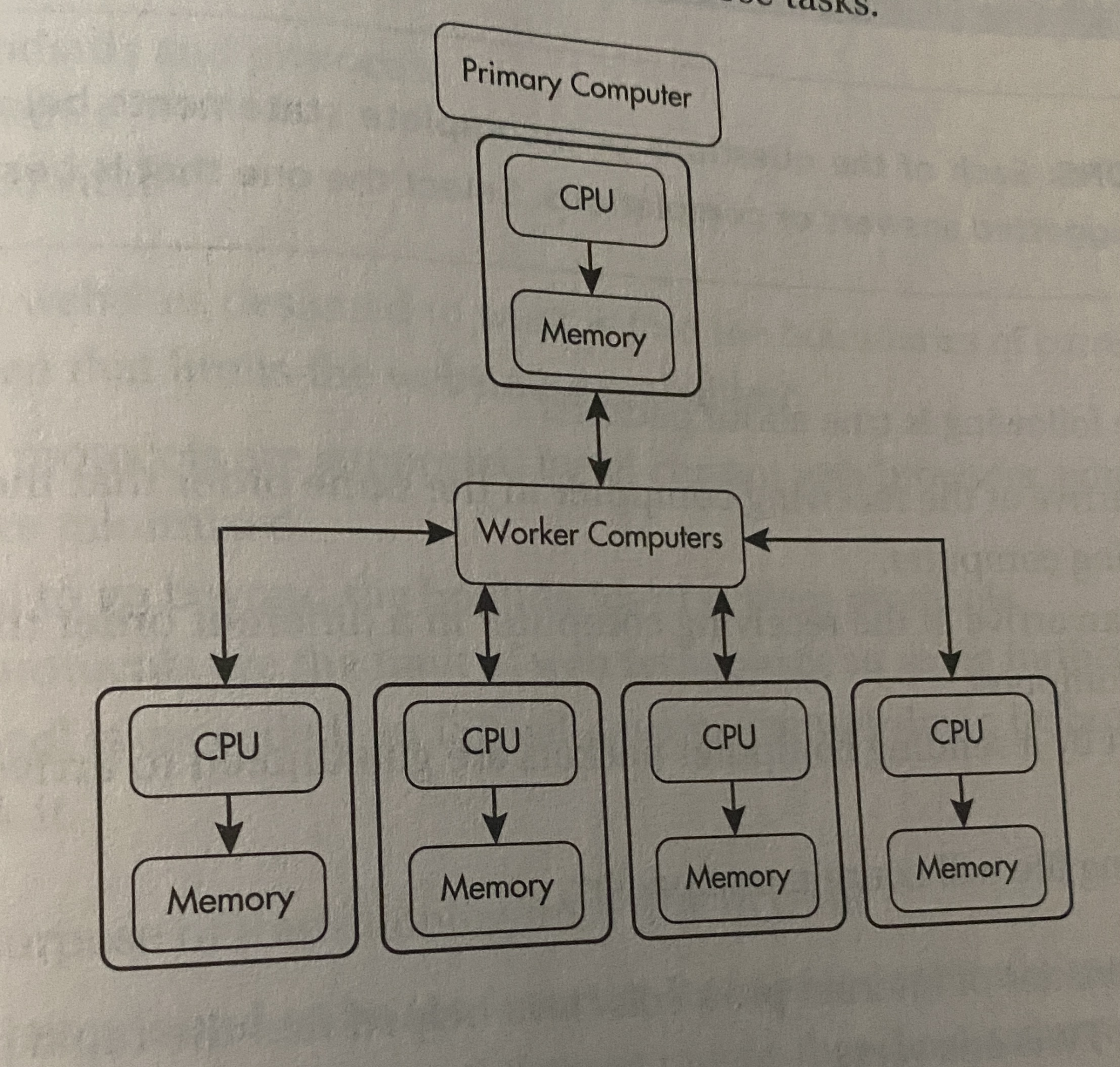
-
-
BIG IDEA 5. Impact of Computing
-
The world wide web
-
Use of the internet and WW are changing all the time
-
Have forever changed how we do business and how people einteract
-
-
Both positive and negative effects of the internet
-
-
Digital divide
-
Differences in acces to technology
-
Including access to comps and internet
-
-
Variables that affect digitale divide:
-
Infrastructure: some parts of the world do not have access to the internet
-
Education: a person could have access to the internet but not have the education ot use it
-
Indifferent: a person could have access to the internet but choose not to use it
-
Cost: the cost of accessing the internet can be unafforadable
-
-
Efforts are being made to reduce the digital divide
-
EX:
-
Google Project Loon uses balloons at the edge of space to provide infrastructure to to places around the world without internet access
-
-
-
Ethical concern
-
Official government policy is being announced on the internet,
-
Poepl without internet acces remain in the dark
-
-
-
-
Beneficial and harmful effects
-
Computing inncovations can have both beneifical and harmful effect on Societies, Cultures, economies
-
An impact, result or outcome
-
-
Beneficial results are contextual and terpertive
-
Identification includes both the classification of the effect as either beneficial or harmful and justification for that classification
-
-
An impact beyond their intended purpose
-
Computing algorithms can have unintended impacts
-
Internet’s original purpose was to be used exclusively by academic, government, and scientific communities. 🥶🥶🥶🥶
-
Innovations have changes way people do tasks
-
Teachers no longer have to hand calc grades
-
-
Effects can be societal, economic, and cultural and can be connected to a group of individuals
-
The impact of social media online access varies in different countries and in diff socioeconomic groups
-
Mobile, wireless and networked computing have an impact on innovation throughout the world
-
The global distribution of computing resources raises issues of equity, access and power
-
Groups and individuals are affected by the digital divide
-
Networks adn infrastructure are supported by both commercial and governmental initiatives
-
-
People create computing innovations and cannot possible consider all possible uses of their innovation
-
Rapid sharing of a programme with many usrs can result in significatn impacts beyondthe intended purpose
-
Control over the information of a large group is hard to police
-
-
-
Human Bias
-
Computi9ng information reflect existing human bias
-
Algorithms are helping people make their decisions that can have extreme ramifications
-
Programmers should take action to reduce bias at all levels of development
-
-
Crowdsourcing
-
Practice of obtaining input or information from many people via the internet
-
Accuracy of answers will vary
-
-
Offerns new models for connecting business with funding
-
Ubr connects drivers with people who need rides
-
-
Can connect social causes with funding
-
A site funds a robotics team
-
-
Easy to post false causes
-
-
Citizen science
-
Scientific research using public participation in scientific research
-
Conducted in whole or by part of individuals
-
Many may or may not be scientists
-
-
Contribute relavent data to research using their own computing devices
-
Data collected is not always technical
-
-
-
Legal and Ethical Concerns
-
Material created on a computer is the intellectual property of the creator or organization
-
Ease of access and distribution of digitized information raises intellectual property concerns regarding ownership value, And use.
-
Algorithms on legitimate sharing sites have an obligation to safeguard intellectual property and remind the illegally shared content from their site
-
-
Plagiarism
-
Use of material created by someone else without permission and presented as one’s own
-
Doing this with code can have legal consequences
-
Napster did not have intellectual property and were closed and heavily fined
-
-
Situations in which materials created by someone else can be used legally
-
Creative Commons
-
an American nonprofit dedicated to expanding the range of creative works available for others to build upon and share legally
-
PUBLIC COPYRIGHT LISCNECE
-
Allows for free distribution of copyrighted work
-
Gies people theright to USE, SHARE, AND BUILD UPON, an authors work
-
Allow creators to communicate which rights they reserve and whcih rights they waive for ht ebenefits of recipients or other creators
-
-
Can vary from letting others copy, distribute, display and perform only original copies of work while not allowing modification without the authors’ permission to allowing for modification if credit is given to the author
-
6 DIFF LEVELS OF THIS LISCENCE
-
Common in education
-
Where teachers share their lessons for students
-
-
Not used when seeking profit
-
Can bring recognition to author which could result in a profit
-
-
-
Open source are programs that are made freely available and may be redistributed and modified
-
Open access is online research output free of all restrictions on access and free of many restrictions on use
-
Suhc as copyright or liscence restrictions
-
-
-
Malicious information can disguise itself as legitimate info, making it hard to figure out what is real
-
Raises legal and ethical concernse
-
-
Computing innovations taht have raised legal and ethical concerns include
-
Developmenet of software that allows access to digital media downloads and streaming
-
Alogirhtms that include bias
-
Existence of computing devices that collect and analyze data by continuously monitoring activities
-
-
-
Safe Computing
-
Security is needed to protect the confidentiality, integrity, and availability of info
-
Protects data from cuner attacks and hacking
-
Privacy is the right to control data generated by one’s usage of computing innovation and restrict the flow of that data to third parties
-
-
Privacy and sec are concerns with any internet interaction
-
Personally identifiable information
-
Information about an indvudial that identifies, links, relates, or describes that person
-
Ss number
-
Age
-
Race
-
Phone number
-
Med info
-
Financial info
-
Biometric data
-
-
Can be processed and analyzed
-
Gain insight on how to interact with customers
-
-
PII is sold to targeted advertisers
-
Ethical concerns about how companies handle the sensitive info of their customers
-
-
-
Once info is online, it becomes difficult to delete
-
Technology enables the collection, use, and exploitation of information about, by and for individuals, groups, and instructions.
-
Search engines can record and maintain a history of searches made by users
-
Websites can record and maintain a history of individuals who have viewed their pages
-
Devices, websites, adn networks can collect info ab a user’s loc
-
-
Metadata can reduce privacy of the user if rapidly shared
-
Multifactor authentication
-
Method of computer access control in which a user is granted access only after suicccessfulyy presenting several pieces of the following 2 categories
-
Knowledge: smth that the user knows
-
Possession: smth that the user has
-
Inherence: smth the user is
-
-
Requires at least 2 steps
-
Each step adds a layer of security
-
-
Digital certificate authorities issue digital certificates that validate the ownership of encryption keys used in secure communications and are based on a trust model
-
-
-
Encryption
-
Uses cryptographic algorithms to encrypt data
-
Process of encoding data to prevent unauthorized access
-
-
Decryption
-
The process of decoding the data
-
-
Symmetric key encryption
-
Uses the same key for both encryption and decrypotion
-
Relies on bith sides keeping the key a secret
-
-
Public Key Encryption
-
Uses two keys
-
One private
-
Used for decryption
-
-
One public
-
Anyone with the public key can encrypt data
-
-
-
-
Malware
-
Malicious software intended to damage a computing system or take partial control of its operations
-
Spread over..
-
Email
-
Executables
-
Instant messages
-
Social media
-
Freeware
-
Shareware
-
Etc
-
-
Used as cyber weapons
-
Searched for outdated software with unpaatched sec flaws that can be exploited to compromise those systems
-
-
Real world systems have errors or design flaws that can be exploited
-
-
Computer Viruses
-
Malicious programs taht can copy temselves and gain access to computer in an unauthorized way
-
Viruses often perform some type of harmful activity on infected host computers
-
Attach themselves to legitimate programs and start running independently on a computer
-
-
Can alter the way computer operates or stop it from working entirety
-
-
Phishing
-
Technique that directs users to unrelated sites that trick the user into giving personal data
-
Pose as legitimate sources
-
Acces sensitive online information
-
-
Often update their tactics, so they can be hard to identify
-
Commonly involves a malicious link that prompts to download a malware or other harmful things
-
-
Keylogging
-
Use of a program to record every keystroke on a computer in order to gain fraudulent access to pwd
-
Can be hardware
-
Installed inbetween the keys and keyboard
-
Cannot be detected by software
-
-
-
Rogue Access Point
-
Wireless Point on a public network in which data can be intercepted, analyzed, and modified unauthorized by a secure network
-